WAN link load balancing
WAN link load balancing
In the same way that incoming traffic can be load balanced, outgoing or WAN traffic can also be load balanced and for the same three reasons.
1. Reduce the places in the work flow where a single point of failure can bring the process to a halt.
2. Expand the capacity of the resources to handle the required workload.
3. Have it configured so that the process of balancing the workload is automatic.
Often, it can be just as important for an organizations members to be able to access the Internet as it is for the denizens of the Internet to access the Web facing resources.
There is now a WAN Load Balancing feature located in the Network section of the GUI (“WAN LLB”).
As part of the new WAN Load Balancing feature, the FortiOS 5.2 Router > Static > Settings GUI page has been removed. WAN Load Balancing should be used instead of the 5.2 ECMP Load Balancing Method settings. The 5.2 Link Health Monitor definitions are now only available from the CLI.
WAN links
The basis for the configuration of the virtual WAN link are the interfaces that comprise it. As interfaces are added to the “wan-load-balance” interface, they are added into the calculations that comprise the various algorithms used to do the load balancing.
- While most of the load balancing algorithms are based on equal distribution or weighted distribution, spill over does rely on which interface is first in the sequence, so this should be kept in mind when adding the interfaces.
- The interfaces in the virtual WAN link can be disabled if necessary if work needs to be done on an interface without interfering with the performance of the link.
- There is no requirement that the interfaces be those labeled on the hardware as WAN interfaces.
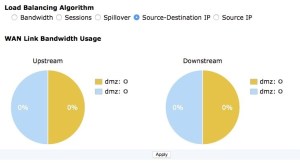
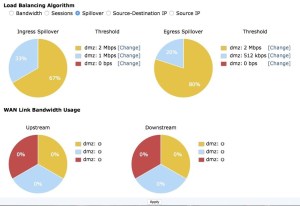
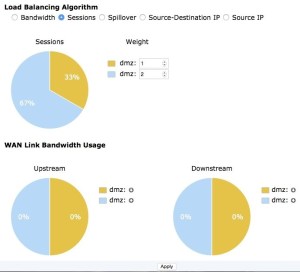
- In the GUI, to help analysis the effectiveness of the algorithm being used and its configuration, there is a graphic representation of the bandwidth usage of the link.
Load balancing algorithm
Once the interfaces involved has been configured the next step is to determine how the workload will be distributed. 5 load balancing algorithms are available to choose from.
Bandwidth
This is a very straight forward method of distributing the work load based on the amount of packets going through the interfaces. An integer value assigns a weight to each interface. These weights are used to calculate a percentage of the total bandwidth that is directed to the interface.
Example:
- There are 2 interfaces
- Interface #1 is assigned a weight of 5 because it is a 5 MB connection. (There is no requirement to match the weight to the capacity of the connection. It is just a simple way of optimizing the differing capacities in this case.)
- Interface #2 is assigned a weight of 3 because it is a 3 MB connection.
- The total weight is 8 so interface #1 gets 5/8 (63%) and interface #2 gets 3/8 (38%) of the traffic.
Sessions
The session algorithm is similar to the bandwidth algorithm in that it also uses an integer value to assign a weight to each interface. The difference is that the number of sessions connected is what is being measured and not the packets flowing through the interfaces.
Spillover
Spillover is a method where a threshold is set for an interface (in kbps) and if the amount of traffic bandwidth exceeds the threshold any traffic bandwidth beyond that threshold is sent out through another interface.
It might be simple to just consider the outgoing or egress traffic when determining a threshold but two facts must be taken into consideration.
1. A simple request going out the interface can be responded to with significantly more data coming back from the other direction.
2. Internet connections come in a variety of configurations, many of which have different levels of allowed bandwidth capacity between the upload and download directions.
For these reasons, the FortiGate allows for the setting of both egress and ingress thresholds for bandwidth.
Source–destination IP
The source-destination IP algorithm tries to equally divide the traffic between the interfaces included in the virtual WAN interface. It used the connection criteria of the source and destination IP address combinations as a way of sorting the traffic.
Example:
- 10.10.10.10 to 1.1.1.2 gets sent out one interface
- Subsequent traffic going from 10.10.10.10 to 1.1.1.2 would also go out that same interface
- The next session to connect through the WAN could be either:
- 10.10.10.27 going to 1.1.1.2
- 10.10.10.10 going to 1.1.1.15.
Either one of the connections in the next session, even though they might match the source or the destination IP address do not match both. Traffic with the next unique combination of source and destination IP address would be sent out the other interface. It would go back and forth like this as new traffic and combinations comes in.
Source IP
The source IP address works just the same as the source-destination IP algorithm but it only concerns itself with the source IP address of the connection.
Priority rules
Some traffic requires that it come from a consistent or specific IP address to be processed properly. Because the different WAN interfaces will have different IP addresses there needs to be a way to override the unpredictability of the load balancing algorithms. This is done by using priority rules
Packets can be checked prior to being assigned an interface by the algorithm. If certain source and/or destination criteria matches the priority rules, the packets can be assigned to an outgoing interface as determined by the rule.
Priority rules can be configured under Network > WAN LLB Rules. The source criteria that can be checked are:
- Source address
- User Group
The destination criteria that can be checked are:
- Whether it’s address-based
- Destination address
- Protocol number
- Whether it’s cloud application-based
- The cloud application
Cloud applications
Cloud applications are a new object that can be used and configured on a FortiGate. There are a limited number of places that they can be used as a means of directing traffic and Virtual WAN links are one of them.
Estimated Bandwidth
An optional parameter has been added that allows users to set the estimated uplink and downlink bandwidths of a WAN interface.This setting is available in both the GUI and the CLI.The range of the setting is from 0 to 16776000.
In the GUI, the there are two fields next to Estimated Bandwidth; one for Kbps Upstream and one for Kbps Downstream.
In the CLI, the fields can be set by using the following syntax:
config system interface edit <wan interface>
set estimated-upstream-bandwidth <integer from 0 – 16776000> set estimated-downstream-bandwidth <integer from 0 – 16776000> end
end
Status check
In order for the load balancing to be effective,there needs to be a constant monitoring of the health and status of the links that make up the virtual WAN link. Customized status checks can be configured to check on health of various aspects the traffic flow going through the link. Using either ICMP packets (PING) or HTTP requests to a designated server, the check can analyze one of the criteria: latency, jitters or packet loss. Once the health reaches a specified threshold, the interface can be automatically removed from the virtual WAN link so that the algorithm is not sending traffic to a failed interface and bring down communications for a portion of the FortiGate’s clientele.
Health Check (266883 299426)
A health check option has been added to the Virtal WAN link feature. The check is configured in the CLI as follows:
Config system virtual-wan-link
set fail-detect [enable | disable]
set fail-alert-interfaces (available only if fail-detect is enabled)
config health-check
edit [Health check name]
set server <string>
set protocol [ping | tcp-echo | udp-echo | http | twamp]
Some of the protocol options cause additional settings are made available.
http
twamp
set port
set http-get set http-match
set port
set security-mode[none | authentication]
The security-mode setting authentication generates yet another potential setting, password.
set password
set packet-size
The next settings are available for all protocols
set interval <integer> set timeout <integer> set failtime [1 – 10]
set recoverytime [1 – 10]
set update-cascade-interface [enable | disable]
set update-static-route [enable | disable]
set threshold-warning-latency <integer 0-4294967295> set threshold-alert-latency <integer 0-4294967295> set threshold-warning-jitter <integer 0-4294967295> set threshold-alert-jitter <integer 0-4294967295>
set threshold-warning-packetloss <integer 0-4294967295> set threshold-alert-packetloss <integer 0-4294967295> end
end end





Nhận xét
Đăng nhận xét