Centralize authorized_keys file on Linux / Unix system
Authorized_keys are important files which has the information of
public keys for public key authentication. By default location is
~/.ssh/authorized_keys. Here, ~ is users default home directory in
system.
While working on SSH, we got requirement to centralize the authorized_keys of all users existing in system. In most of the system for SSH we use the OpenSSH package. Hence, the default location for SSH config file is
Centralizing the authorized_keys for all users is quite easy. We believe you already have some experience on public and private ssh key pairs, because for access user need SSH private key.
For example , I found some valid users from system like –
First take backup of /etc/ssh/sshd_config file. In case, if something goes wrong we can revert back by copying the backup file to original.
For root user , now we will centralize authorized_keys. Follow the given below steps
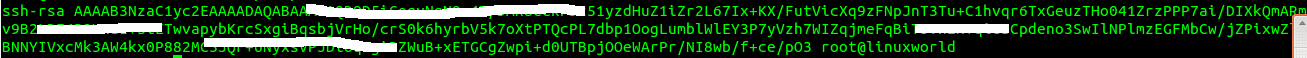
For reference, the ssh public key appear like this. Please take it as an example only.
Set centralized authorized_keys for all users
Just as we have completed in above steps, almost same step you have to follow for all users. For example, our user name is mike . Let’s set authorized_keys file for mike
Same steps follow for each users. In case, you are good in scripting you can easily achieve this by using for..loop .
While working on SSH, we got requirement to centralize the authorized_keys of all users existing in system. In most of the system for SSH we use the OpenSSH package. Hence, the default location for SSH config file is
/etc/ssh/sshd_config .Centralizing the authorized_keys for all users is quite easy. We believe you already have some experience on public and private ssh key pairs, because for access user need SSH private key.
Step 1: List the users name exist in system
Gather the information of existing users from/etc/passwd file . Make a list of users to whom you want to give access in system with SSH key authentication method.For example , I found some valid users from system like –
joe mike Joseph
Step 2 : Create a new directory
Create a new directory inside /etc/ssh . This we will use this directory for placing all users keys.mkdir -p /etc/ssh/KEYS
Step 3: Edit the sshd_config file
Now we will edit the sshd_config file. We will editAuthorizedKeysFile parameter in /etc/ssh/sshd_config file. First take backup of /etc/ssh/sshd_config file. In case, if something goes wrong we can revert back by copying the backup file to original.
cp -p /etc/ssh/sshd_config /etc/ssh/sshd_config.$(date +%F).backupQuickly checking if AuthorizedKeysFile parameter exist in file.
egrep -v '^#|^$' /etc/ssh/sshd_config |grep AuthorizedKeysFileIf AuthorizedKeysFile parameter exist in system then edit in below given format or otherwise add below given line in /etc/ssh/sshd_config
AuthorizedKeysFile /etc/ssh/KEYS/%u
Step 4: Create directories matches with user name
Create directories matches with user name whose authorized_keys file you want to centralize.For root user , now we will centralize authorized_keys. Follow the given below steps
mkdir -p /etc/ssh/KEYS/root chown root:root /etc/ssh/KEYS/root chmod 755 /etc/ssh/KEYS/root
touch /etc/ssh/KEYS/root/authorized_keys chmod 644 /etc/ssh/KEYS/root/authorized_keys chown root:root /etc/ssh/KEYS/root/authorized_keysGet the public key content and paste in /etc/ssh/KEYS/root/authorized_keys file.
For reference, the ssh public key appear like this. Please take it as an example only.
Set centralized authorized_keys for all users
Just as we have completed in above steps, almost same step you have to follow for all users. For example, our user name is mike . Let’s set authorized_keys file for mike
mkdir -p /etc/ssh/KEYS/mike chown mike:mike /etc/ssh/KEYS/mike chmod 755 /etc/ssh/KEYS/mike
touch /etc/ssh/KEYS/mike/authorized_keys chmod 644 /etc/ssh/KEYS/mike/authorized_keys chown mike:mike /etc/ssh/KEYS/mike/authorized_keysGet the public key content for user called mike and paste in /etc/ssh/KEYS/mike/authorized_keys file.
Same steps follow for each users. In case, you are good in scripting you can easily achieve this by using for..loop .
Step 5: Now reload the ssh service
In CentOS 7 / RHEL 7systemctl reload sshd
In CentOS 6 / RHEL 6service sshd reload
In Ubuntu / Debian sudo service ssh reload

Nhận xét
Đăng nhận xét